
Computers are everywhere – cars, buses, trains, planes, etc. and if you look at IoT (Internet of Things), you will find them even in your most personal items, such as wearable devices. Laptops, mobile phones, and tablets are modern-day artifacts of what used to be the huge mainframes of the past, bringing the convenience and power of computing in the palm of your hands. The use of computers has transformed even household items such as televisions, microwaves, and refrigerators.
The idea behind all the friendly user interfaces and services offered by these systems can be summed with the word “Code”. Code happens to be the foundation of all computing, controlling the ins and outs of all things we see as computing devices. Modern computers are no more static, they are being constantly upgraded with new programming releases, and often, you do not even know when the update happens.
Where the code is coming from?
It is hard to imagine that the code that controls your vehicle, smartphone and household items may be downloaded and upgraded at any time, without you knowing when it happens. Who published the software? Do you know? Can your techie friends tell?
And most notably, can your computing devices make out?
We depend on these machines and gizmos for everything – can they make out the source of publication of the code that runs the applications they provide? How do these devices figure out if the code is genuine? Can the software they run be trusted to be safe?
What is a code signing certificate?
The answer to trusting the software you distribute or run is Code Signing Certificates.
Code Signing Certificates are digital signatures that are applied to the code of a software/application to protect it from meddling. It makes use of complex mathematical techniques to attach a digital ID of the publisher who wrote or distributed the code. This guarantees the authenticity of the code and builds the user’s trust in the publisher or author of the software.
Code signing solves the tough question and ensures that no rogue download sites get hold of a copy of your application and start spreading your code bundled with malware. Someone with malicious intent may upload your software to a rogue website so people can get their hands on it for free, but they may decide to plug in some adware or virus as part of the distribution. If the software you develop or publish is a favorite of your customers, the malware publisher has hit the bonanza – they can easily hide their harmful software behind your posted code.
Not just you, even your loyal users will find it impossible to determine if the code they just downloaded is authentic and can be entrusted as coming from you.
The related risk is genuine – unsigned code does get used by hackers for launching cyber-attacks all the time. Impersonating malicious code as safe, that users may trust to run on their devices, has been a popular distribution mechanism for spreading malware. A lot of people look for popular software such as Microsoft Office, and Adobe tools online, and virus distributors take full advantage of this. It is hard to find someone who has not downloaded software from the non-original source; everyone has friends who have been infected after getting such “free” applications.
How Do Code Signing Certificates Work?
A Code signing certificate works just like an SSL certificate.
A Code Signing Certificate is associated with a distinct private key kept that is kept secret by the publisher of the software/application.
The private key produces a unique signature for every code sample; the key actually puts a signature on the “hash” of the code. Code signing attaches the result of the process to the code – it does not encrypt your software files.
When the recipient of your software runs the application, their operating system (iOS, Android, Windows, Linux, etc.) verifies the signature and displays the publisher’s information – this happens by the hashing of the software code and matching it with the signature decrypted using your public key. This helps the user determine the origin of the code, so they can make an informed decision about executing it.
Code signing provides your software with the identity of the code source. In the end, it is up to the customers receiving the application to decide if they trust the publisher. Just having a signature on a program does not automatically mean that it may not cause harm. Anyone can sign a virus and publish it – just knowing the distributor of the software does not mean it is harmless to use.
Code signing only guarantees that the code has been delivered precisely as distributed by the code publisher.
Digital signatures can be cryptographically enforced. This means the devices reading a code signature can tell if it is genuine or not.
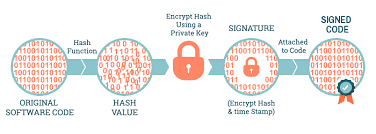
Here is how the process looks like:
- You first apply for your digital certificate – approach any trusted CA you trust for this.
- Before issuing your code signing certificate, the CA will validate your claim to confirm you are who you present yourself as.
- Once the CA issues your code signing certificate, your developers will need to install it on their machine. All development platforms include tools to help developers install digital certificates and sign their code.
- Your developers are now ready to sign their code using the digital signature. They can use one of the tools provided for their platform to sign the code before releasing it to the end-users. Once done, they are ready to deliver the application.
- They can adopt any mechanism to get the application in the hands of your users – internet, flash drive, CD, or any other method you prefer. When your customers execute your code, they will see your ID – and can trust the authenticity of the code you have provided.
Remember that developing and distributing software makes you part of not only a vast ecosystem of users, computers, and other devices but bad actors as well. The weakest links in the distribution chain will be under constant attack, and security requirements and expectations will always be increasing. Stay ahead of the curve by adopting code signing for all your applications. Your users will appreciate it, and when attacks are prevented, you will be relieved.
Benefits of Code Signing Certificate
Code signing helps both the publisher and the end-user.
The problem as a publisher
Your written code gets distributed all around the globe – your customers depend on you for their software, and they trust your code. How do you ensure that your end-users get the exact copy of the code you distributed, with no adulteration?
The problem as a customer?
How do you trust you are getting the same version of the code as published by your software author? What if someone introduced some malware before you got it?
Once you sign your code, you can trust that the software gets to your customers without any contamination, and you do not lose them to a malware being introduced by some 3rd party.
Your customers can stay safe as they know they have what was sent out.
Code signing is an excellent manner of securing your code to gain and retain the trust of your customers. It works perfectly on most platforms while providing the assurance of the origin and trustworthiness. While signing your software, do not use self-signed certificates (which are not backed by a trusted CA). Also, keep the best code signing practices in mind when implementing your software release process – like not sharing your private code signing key outside your core development team.
